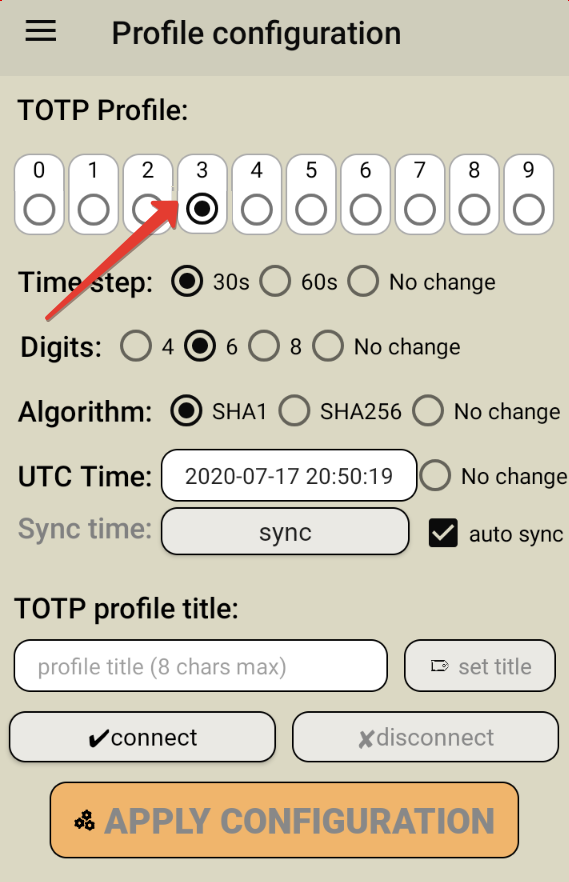
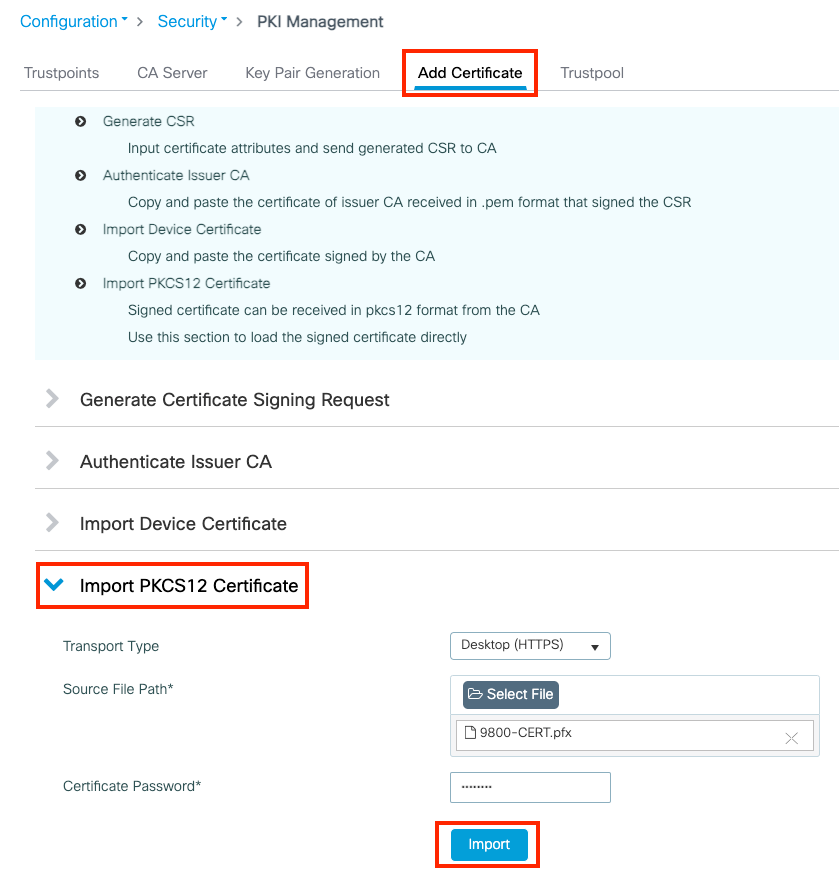
Analysis of Inappropriate Usage of Cryptographic Primitives in Indian Mobile Financial Applications | SpringerLink
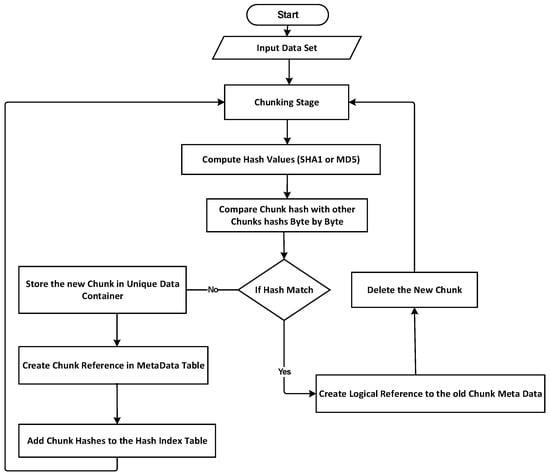
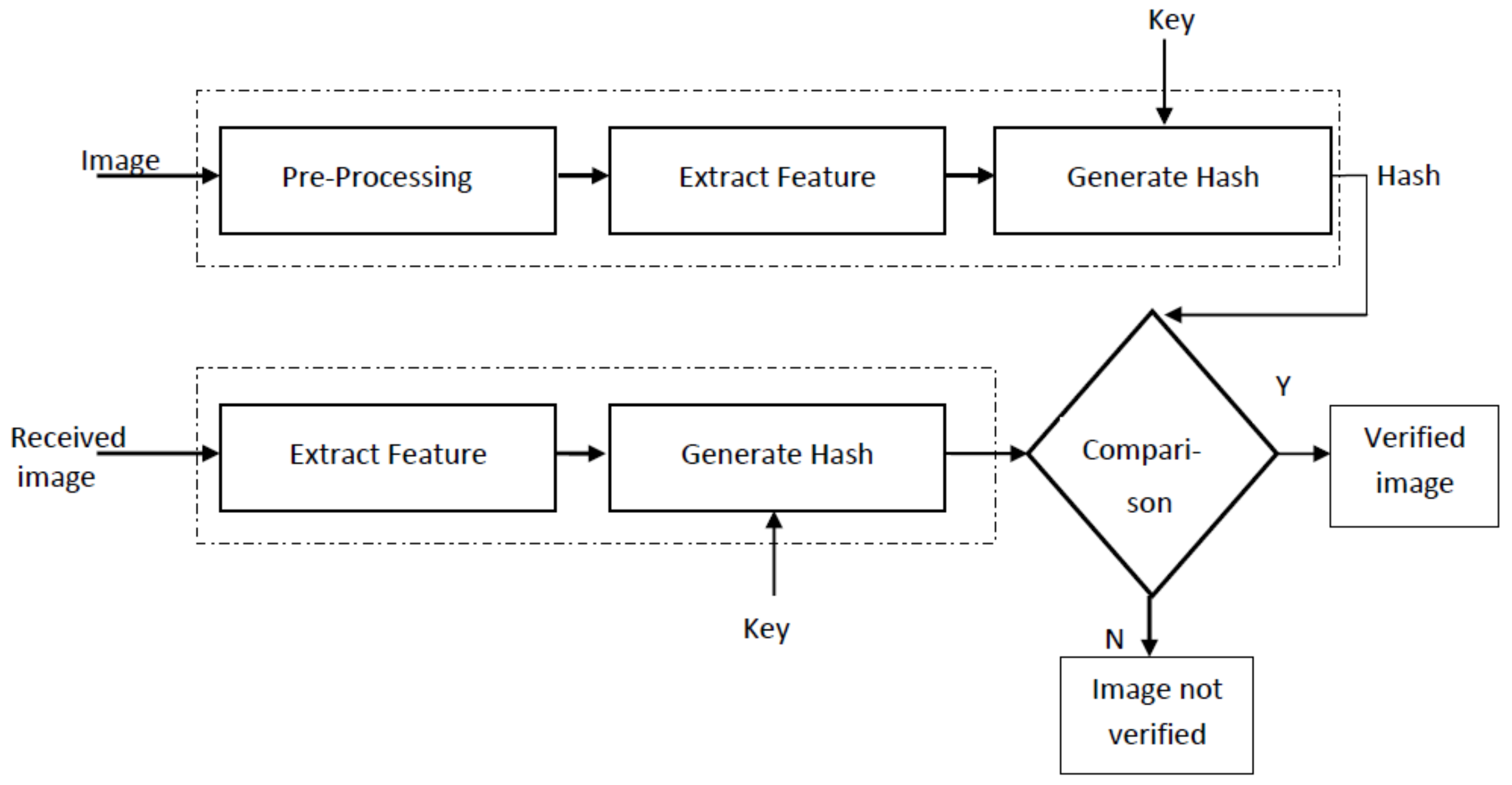
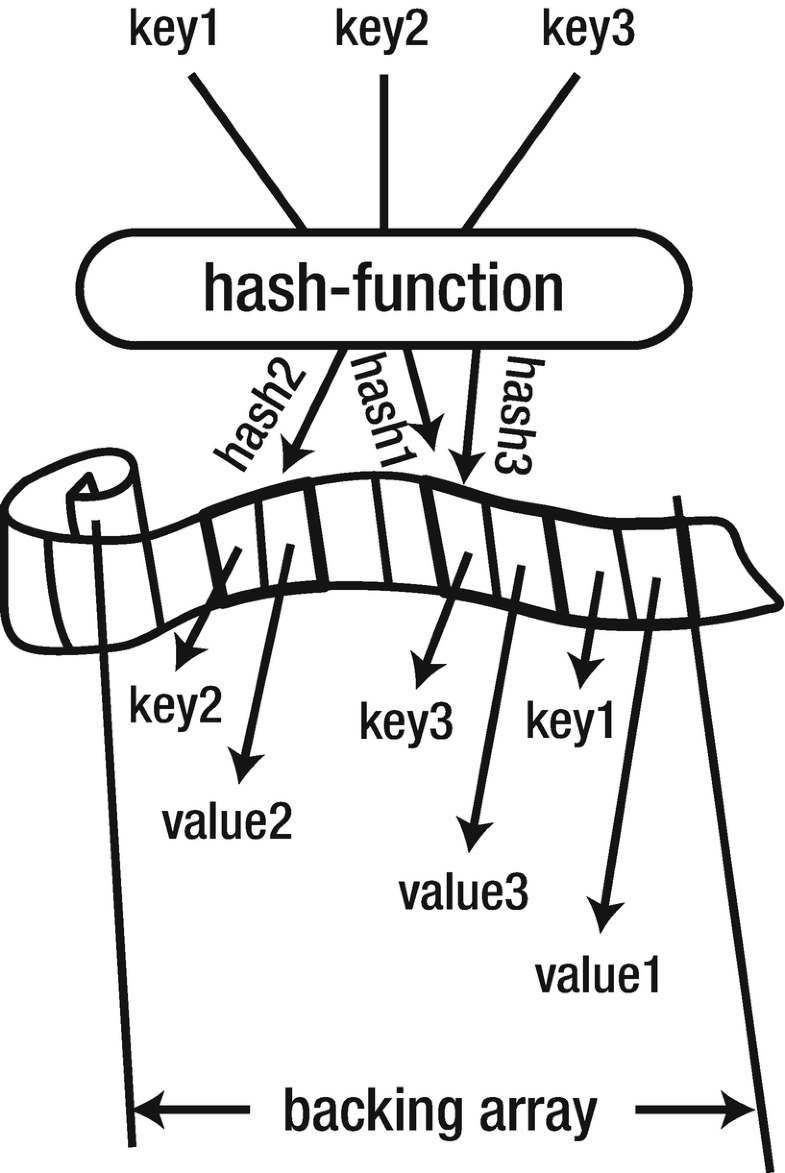
Symmetry | Free Full-Text | Fingerprint-Based Data Deduplication Using a Mathematical Bounded Linear Hash Function | HTML
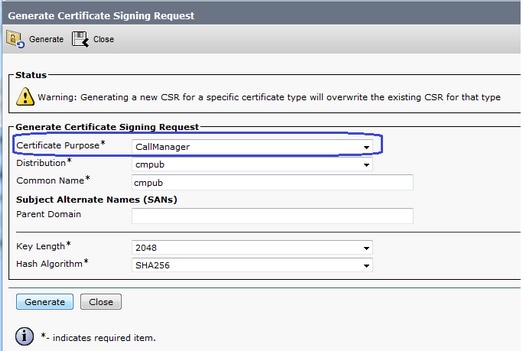
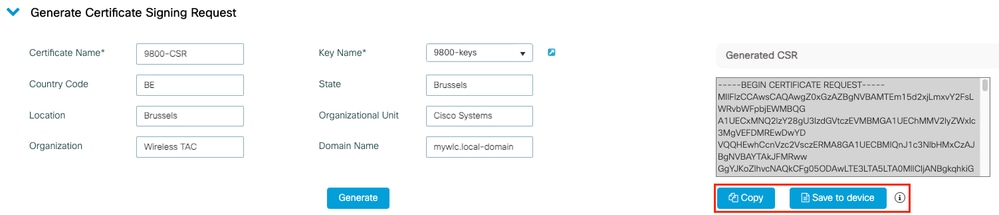
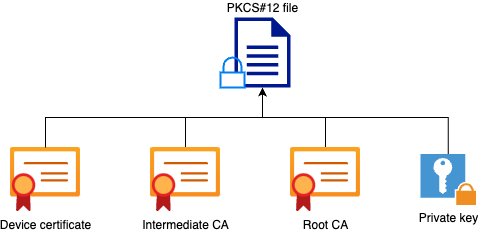
Signierte Zertifikate der Enterprise CA (Drittanbieter-CA) für SIP TLS und SRTP zwischen CUCM, IP-Telefonen und CUBE konfigurieren und Fehlerbehebung dafür durchführen - Cisco