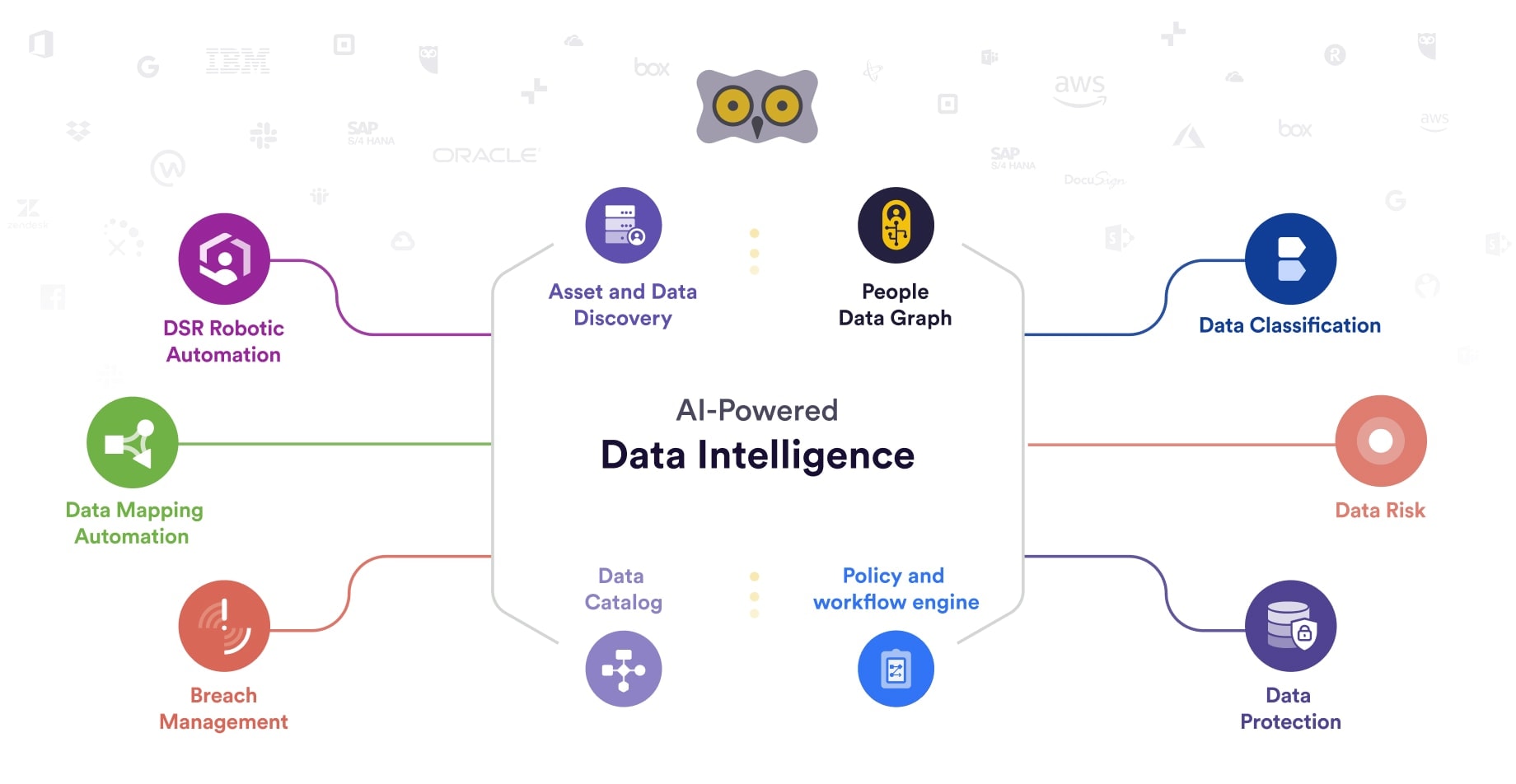
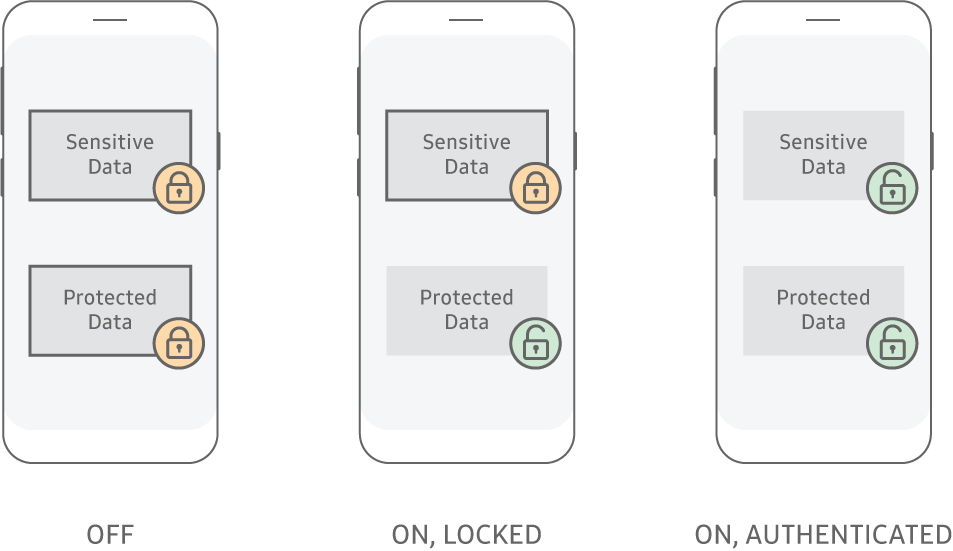
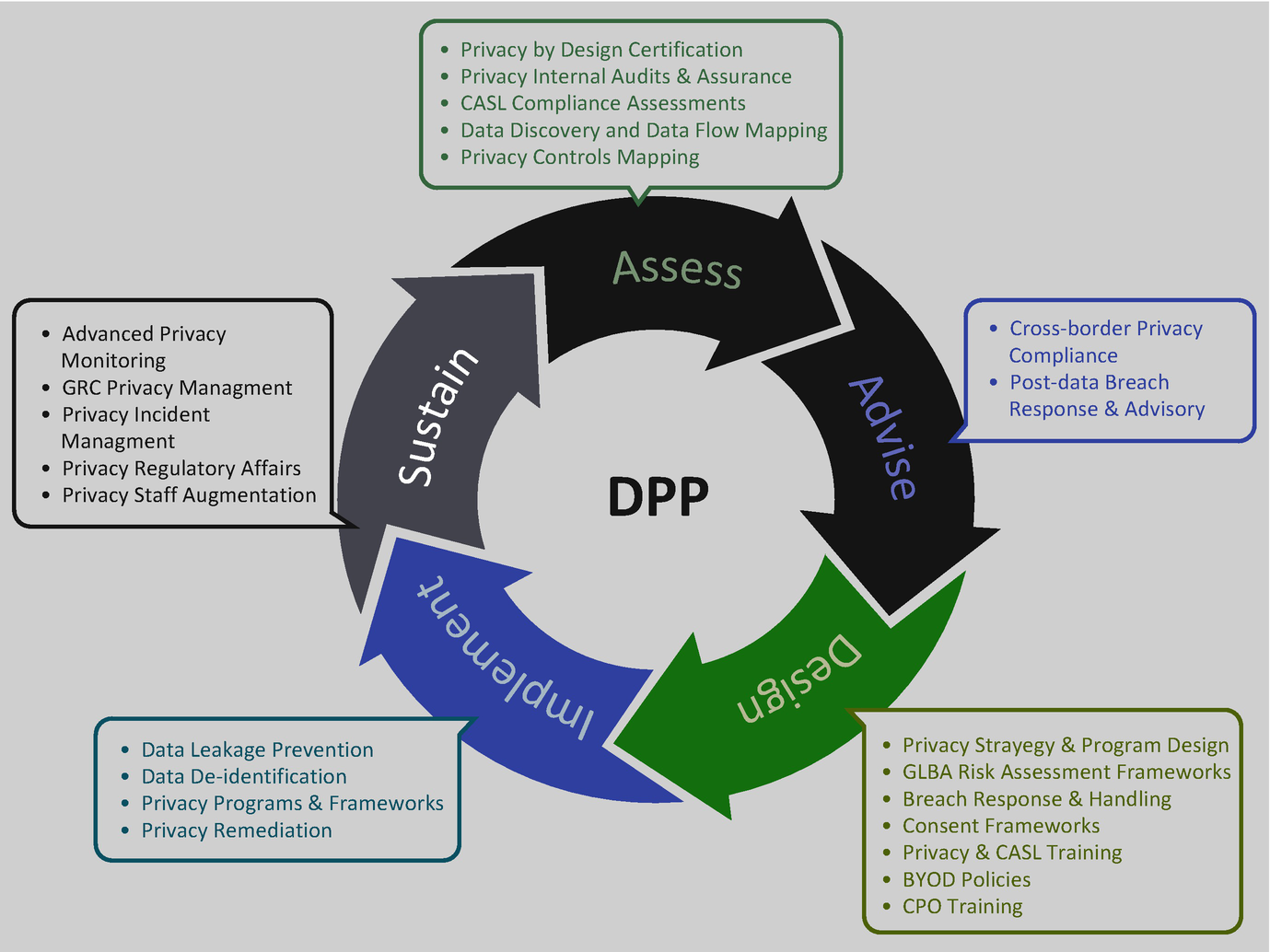
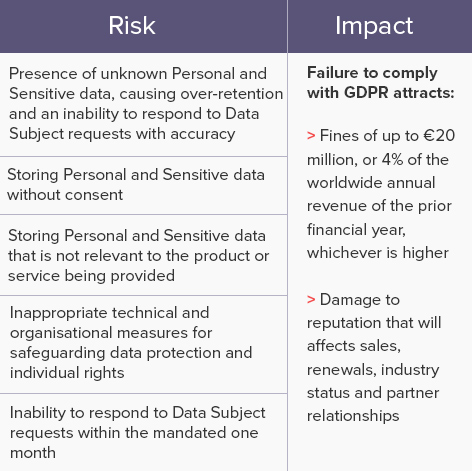
GDPR Concept Illustration. General Data Protection Regulation. the Protection of Personal Data, Checklist Infographics Stock Vector - Illustration of monitor, brochure: 112275411

Anonymisation and open data: an introduction to managing the risk of re-identification (report) – The ODI

Emergency Remote Teaching: a study of copyright and data protection policies of popular online services (Part II) - Kluwer Copyright Blog